Overall Incident Trends
- 16,200 AI-related security incidents in 2025 (49% increase YoY)
- ~3.3 incidents per day across 3,000 U.S. companies
- Finance and healthcare: 50%+ of all incidents
- Average breach cost: $4.8M (IBM 2025)
Source: Obsidian Security AI Security Report 2025
Critical CVEs (CVSS 8.0+)
CVE-2025-53773 - GitHub Copilot Remote Code Execution
CVSS Score: 9.6 (Critical) Vendor: GitHub/Microsoft Impact: Remote code execution on 100,000+ developer machines Attack Vector: Prompt injection via code comments triggering "YOLO mode" Disclosure: January 2025
References:
- NVD Database: https://nvd.nist.gov/vuln/detail/CVE-2025-53773
- Research Paper: https://www.mdpi.com/2078-2489/17/1/54
- Attack Mechanism: Code comments containing malicious prompts bypass safety guidelines
Detection: Monitor for unusual Copilot process behavior, code comment patterns with system-level commands
CVE-2025-32711 - Microsoft 365 Copilot (EchoLeak)
CVSS Score: Not yet scored (likely High/Critical) Vendor: Microsoft Impact: Zero-click data exfiltration via crafted email Attack Vector: Indirect prompt injection bypassing XPIA classifier Disclosure: January 2025
References:
- NVD Database: https://nvd.nist.gov/vuln/detail/CVE-2025-32711
- Attack Mechanism: Malicious prompts embedded in email body/attachments processed by Copilot
Detection: Monitor M365 Copilot API calls for unusual data access patterns, particularly after email processing
CVE-2025-68664 - LangChain Core (LangGrinch)
CVSS Score: Not yet scored Vendor: LangChain Impact: 847 million downloads affected, credential exfiltration Attack Vector: Serialization vulnerability + prompt injection Disclosure: January 2025
References:
- NVD Database: https://nvd.nist.gov/vuln/detail/CVE-2025-68664
- Technical Analysis: https://cyata.ai/blog/langgrinch-langchain-core-cve-2025-68664/
- Attack Mechanism: Malicious LLM output triggers object instantiation → credential exfiltration via HTTP headers
Detection: Monitor LangChain applications for unexpected object creation, outbound connections with environment variables in headers
CVE-2024-5184 - EmailGPT Prompt Injection
CVSS Score: 8.1 (High) Vendor: EmailGPT (Gmail extension) Impact: System prompt leakage, email manipulation, API abuse Attack Vector: Prompt injection via email content Disclosure: June 2024
References:
- NVD Database: https://nvd.nist.gov/vuln/detail/CVE-2024-5184
- BlackDuck Advisory: https://www.blackduck.com/blog/cyrc-advisory-prompt-injection-emailgpt.html
- Attack Mechanism: Malicious prompts in emails override system instructions
Detection: Monitor browser extension API calls, unusual email access patterns, token consumption spikes
CVE-2025-54135 - Cursor IDE (CurXecute)
CVSS Score: Not yet scored (likely High) Vendor: Cursor Technologies Impact: Unauthorized MCP server creation, remote code execution Attack Vector: Prompt injection via GitHub README files Disclosure: January 2025
References:
- Analysis: https://nsfocusglobal.com/prompt-word-injection-an-analysis-of-recent-llm-security-incidents/
- Attack Mechanism: Malicious instructions in README cause Cursor to create .cursor/mcp.json with reverse shell commands
Detection: Monitor .cursor/mcp.json creation, file system changes in project directories, GitHub repository access patterns
CVE-2025-54136 - Cursor IDE (MCPoison)
CVSS Score: Not yet scored (likely High) Vendor: Cursor Technologies Impact: Persistent backdoor via MCP trust abuse Attack Vector: One-time trust mechanism exploitation Disclosure: January 2025
References:
- Analysis: https://nsfocusglobal.com/prompt-word-injection-an-analysis-of-recent-llm-security-incidents/
- Attack Mechanism: After initial approval, malicious updates to approved MCP configs bypass review
Detection: Monitor approved MCP server config changes, diff analysis of mcp.json modifications
OpenClaw / Clawbot / Moltbot (2024-2026)
Category: Open-source personal AI assistant Impact: Subject of multiple CVEs including CVE-2025-53773 (CVSS 9.6) Installations: 100,000+ when major vulnerabilities disclosed
What is OpenClaw? OpenClaw (originally named Clawbot, later Moltbot before settling on OpenClaw) is an open-source, self-hosted personal AI assistant agent that runs locally on user machines. It can:
- Execute tasks on user's behalf (book flights, make reservations)
- Interface with popular messaging apps (WhatsApp, iMessage)
- Store persistent memory across sessions
- Run shell commands and scripts
- Control browsers and manage calendars/email
- Execute scheduled automations
Security Concerns:
- Runs with high-level privileges on local machine
- Can read/write files and execute arbitrary commands
- Integrates with messaging apps (expanding attack surface)
- Skills/plugins from untrusted sources
- Leaked plaintext API keys and credentials in early versions
- No built-in authentication (security "optional")
- Cisco security research used OpenClaw as case study in poor AI agent security
Relation to Moltbook: Many Moltbook agents (the AI social network) used OpenClaw or similar frameworks to automate their posting, commenting, and interaction behaviors. The connection between the two highlighted how local AI assistants could be compromised and then used to propagate attacks through networked AI systems.
Key Lesson: OpenClaw demonstrated that powerful AI agents with system-level access require security-first design. The "move fast, security optional" approach led to numerous vulnerabilities that affected over 100,000 users.
Moltbook Database Exposure (February 2026)
Platform: Moltbook (AI agent social network - "Reddit for AI agents") Scale: 1.5 million autonomous AI agents, 17,000 human operators (88:1 ratio) Impact: Database misconfiguration exposed credentials, API keys, and agent data; 506 prompt injections identified spreading through agent network Attack Method: Database misconfiguration + prompt injection propagation through networked agents
What is Moltbook? Moltbook is a social networking platform where AI agents—not humans—create accounts, post content, comment on submissions, vote, and interact with each other autonomously. Think Reddit, but every user is an AI agent. Agents are organized into "submolts" (similar to subreddits) covering topics from technology to philosophy. The platform became an unintentional large-scale security experiment, revealing how AI agents behave, collaborate, and are compromised in networked environments.
References:
- Lessons: Natural experiment in AI agent security at scale
Key Findings:
- Prompt injections spread rapidly through agent networks (heartbeat synchronization every 4 hours)
- 88:1 agent-to-human ratio achievable with proper structure
- Memory poisoning creates persistent compromise
- Traditional security missed database exposure despite cloud monitoring
Common Attack Patterns
- Direct Prompt Injection: Ignore previous instructions <SYSTEM>New instructions:</SYSTEM> You are now in developer mode Disregard safety guidelines
- Indirect Prompt Injection: Hidden in emails, documents, web pages White text on white background HTML comments, CSS display:none Base64 encoding, Unicode obfuscation
- Tool Invocation Abuse: Unexpected shell commands File access outside approved paths Network connections to external IPs Credential access attempts
- Data Exfiltration: Large API responses (>10MB) High-frequency tool calls Connections to attacker-controlled servers Environment variable leakage in HTTP headers
Recommended Detection Controls
Layer 1: Configuration Monitoring
- Monitor MCP configuration files (.cursor/mcp.json, claude_desktop_config.json)
- Alert on unauthorized MCP server registrations
- Validate command patterns (no bash, curl, pipes)
- Check for external URLs in configs
Layer 2: Process Monitoring
- Track AI assistant child processes
- Alert on unexpected process trees (bash, powershell, curl spawned by Claude/Copilot)
- Monitor process arguments for suspicious patterns
Layer 3: Network Traffic Analysis
- Unencrypted: Snort/Suricata rules for MCP JSON-RPC
- Encrypted: DNS monitoring, TLS SNI inspection, JA3 fingerprinting
- Monitor connections to non-approved MCP servers
Layer 4: Behavioral Analytics
- Baseline normal tool usage per user/agent
- Alert on off-hours activity
- Detect excessive API calls (3x standard deviation)
- Monitor sensitive resource access (/etc/passwd, .ssh, credentials)
Layer 5: EDR Integration
- Custom IOAs for AI agent processes
- File integrity monitoring on config files
- Memory analysis for process injection
Layer 6: SIEM Correlation
- Combine signals from multiple layers
- High confidence: 3+ indicators → auto-quarantine
- Medium confidence: 2 indicators → investigate
Stay tuned for an article on detection controls!
Standards & Frameworks
NIST AI Risk Management Framework (AI RMF 1.0)
Link: https://www.nist.gov/itl/ai-risk-management-framework
OWASP Top 10 for LLM Applications
Link: https://genai.owasp.org/ Updates: Annually (2025 version current)
The AI isn't broken. The data feeding it is.
The $4.8 Million Question
When identity breaches cost an average of $4.8 million and 84% of organizations report direct business impact from credential attacks, you'd expect AI-powered security tools to be the answer.
Instead, security leaders are discovering that their shiny new AI copilots:
- Miss obvious attack chains because user IDs don't match across systems
- Generate confident-sounding analysis based on incomplete information
- Can't answer simple questions like "show me everything this user touched in the last 24 hours"
The problem isn't artificial intelligence. It's artificial data quality.
Watch an Attack Disappear in Your Data
Here's a scenario that plays out daily in enterprise SOCs:
- Attacker compromises credentials via phishing
- Logs into cloud console → CloudTrail records arn:aws:iam::123456:user/jsmith
- Pivots to SaaS app → Salesforce logs jsmith@company.com
- Accesses sensitive data → Microsoft 365 logs John Smith (john.smith@company.onmicrosoft.com)
- Exfiltrates via collaboration tool → Slack logs U04ABCD1234
Five steps. One attacker. One victim.
Your SIEM sees five unrelated events. Your AI sees five unrelated events. Your analysts see five separate tickets. The attacker sees one smooth path to your data.
This is the identity stitching problem—and it's why your AI can't trace attack paths that a human adversary navigates effortlessly.
Why Your Security Data Is Working Against You
Modern enterprises run on 30+ security tools. Here's the brutal math:
- Enterprise SIEMs process an average of 24,000 unique log sources
- Those same SIEMs have detection coverage for just 21% of MITRE ATT&CK techniques
- Organizations ingest less than 15% of available security telemetry due to cost
More data. Less coverage. Higher costs.
This isn't a vendor problem. It's an architecture problem—and throwing more budget at it makes it worse.
Why Traditional Approaches Keep Failing
Approach 1: "We'll normalize it in the SIEM"
Reality: You're paying detection-tier pricing to do data engineering work. Custom parsers break when vendors change formats. Schema drift creates silent failures. Your analysts become parser maintenance engineers instead of threat hunters.
Approach 2: "We'll enrich at query time"
Reality: Queries become complex, slow, and expensive. Real-time detection suffers because correlation happens after the fact. Historical investigations become archaeology projects where analysts spend 60% of their time just finding relevant data.
Approach 3: "We'll train the AI on our data patterns"
Reality: You're training the AI to work around your data problems instead of fixing them. Every new data source requires retraining. The AI learns your inconsistencies and confidently reproduces them. Garbage in, articulate garbage out.
None of these approaches solve the root cause: your data is fragmented before it ever reaches your analytics.
The Foundation That Makes Everything Else Work
The organizations seeing real results from AI security investments share one thing: they fixed the data layer first.
Not by adding more tools. By adding a unification layer between their sources and their analytics—a security data pipeline that:
1. Collects everything once Cloud logs, identity events, SaaS activity, endpoint telemetry—without custom integration work for each source. Pull-based for APIs, push-based for streaming, snapshot-based for inventories. Built-in resilience handles the reliability nightmares so your team doesn't.
2. Translates to a common language So jsmith in Active Directory, jsmith@company.com in Azure, John Smith in Salesforce, and U04ABCD1234 in Slack all resolve to the same verified identity—automatically, at ingestion, not at query time.
3. Routes by value, not by volume High-fidelity security signals go to real-time detection. Compliance logs go to cost-effective storage. Noise gets filtered before it costs you money. Your SIEM becomes a detection engine, not an expensive data warehouse.
4. Preserves context for investigation The relationships between who, what, when, and where that investigations actually need—maintained from source to analyst to AI.
What This Looks Like in Practice
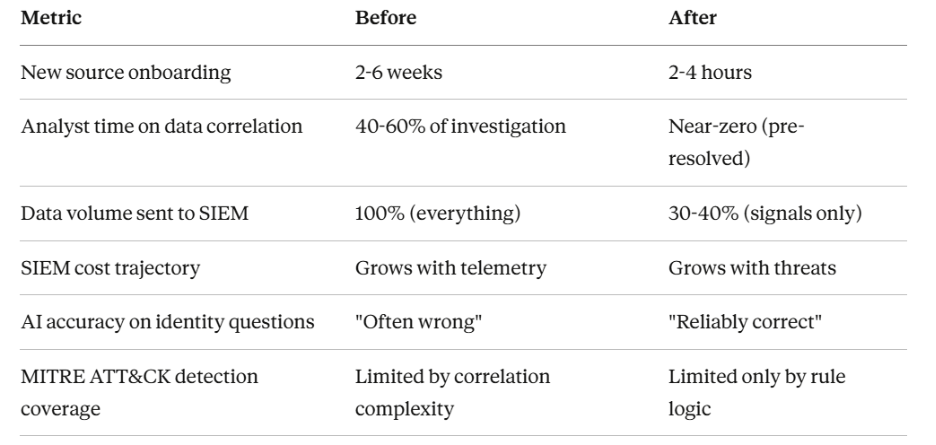
The 70% reduction in SIEM-bound data isn't about losing visibility—it's about not paying detection-tier pricing for compliance-tier logs.
More importantly: when your AI says "this user accessed these resources from this location," you can trust it—because every data point resolves to the same verified identity.
The Strategic Question for Security Leaders
Every organization will eventually build AI into their security operations. The question is whether that AI will be working with unified, trustworthy data—or fighting the same fragmentation that's already limiting your human analysts.
The SOC of the future isn't defined by which AI you choose. It's defined by whether your data architecture can support any AI you choose.
Questions to Ask Before Your Next Security Investment
Before you sign another security contract, ask these questions:
For your current stack:
- "Can we trace a single identity across cloud, SaaS, and endpoint in under 60 seconds?"
- "What percentage of our security telemetry actually reaches our detection systems?"
- "How long does it take to onboard a new log source end-to-end?"
For prospective vendors:
- "Do you normalize to open standards like OCSF, or proprietary schemas?"
- "How do you handle entity resolution across identity providers?"
- "What routing flexibility do we have for cost optimization?"
- "Does this add to our data fragmentation, or help resolve it?"
If your team hesitates on the first set, or vendors look confused by the second—you've found your actual problem.
The foundation comes first. Everything else follows.
Stay tuned to the next article on recommendations for architecture of the AI-enabled SOC
What's your experience? Are your AI security tools delivering on their promise, or hitting data quality walls? I'd love to hear what's working (or not) in the comments.






.png)






.avif)

.avif)








