SIEM migration is a high-stakes project. Whether you are moving from a legacy on-prem SIEM to a cloud-native platform, or changing vendors for better performance, flexibility, or cost efficiency, more security leaders are finding themselves at this inflection point. The benefits look clear on paper, however, in practice, the path to get there is rarely straightforward.
SIEM migrations often drag on for months. They break critical detections, strain engineering teams with duplicate pipelines, and blow past the budgets set. The work is not just about switching platforms. It is about preserving threat coverage, maintaining compliance, and keeping the SOC running without gaps. And let’s not forget, the challenge of testing multiple SIEMs before making the switch and, what should be a forward-looking upgrade, can quickly turn into a drawn-out struggle.
In this blog, we’ll explore how security teams can approach SIEM migration in a way that reduces risk, shortens timelines, and avoids costly surprises.
What Makes a SIEM Migration Difficult and How to Prepare
Even with a clear end goal, SIEM migration is rarely straightforward. It’s a project that touches every part of the SOC, from ingestion pipelines to detection logic, and small oversights early on can turn into major setbacks later. These are some of the most common challenges security teams face when making the switch.
Data format and ingestion mismatches
Every SIEM has its own log formats, field mappings, and parsing rules. Moving sources over often means reworking normalization, parsers, and enrichment processes, all while keeping the old system running.
Detection logic that doesn’t transfer cleanly
Rules built for one SIEM often fail in another due to differences in correlation methods, query languages, or built-in content. This can cause missed alerts or floods of false positives during migration.
The operational weight of a dual run
Running the old and new SIEM in parallel is almost always required, but it doubles the workload. Teams must maintain two sets of pipelines and dashboards while monitoring for gaps or inconsistencies.
Rushed or incomplete evaluation before migration
Many teams struggle to properly test multiple SIEMs with realistic data, either because of engineering effort or data sensitivity. When evaluation is rushed or skipped, ingest cost issues, coverage gaps, or integration problems often surface mid-migration. A thorough evaluation with representative data helps avoid these surprises.
In our upcoming SIEM Migration Evaluation Checklist, we’ll share the key criteria to test before you commit to a migration, from log schema compatibility and detection performance to ingestion costs and integration fit.
How DataBahn Reinvents SIEM Migration with a Security Data Fabric
Many of the challenges that slow or derail SIEM migration come down to one thing: a lack of control over the data layer. DataBahn’s Security Data Fabric addresses this by separating data collection and routing from the SIEM itself, giving teams the flexibility to move, test, and optimize data without being tied to a single platform.
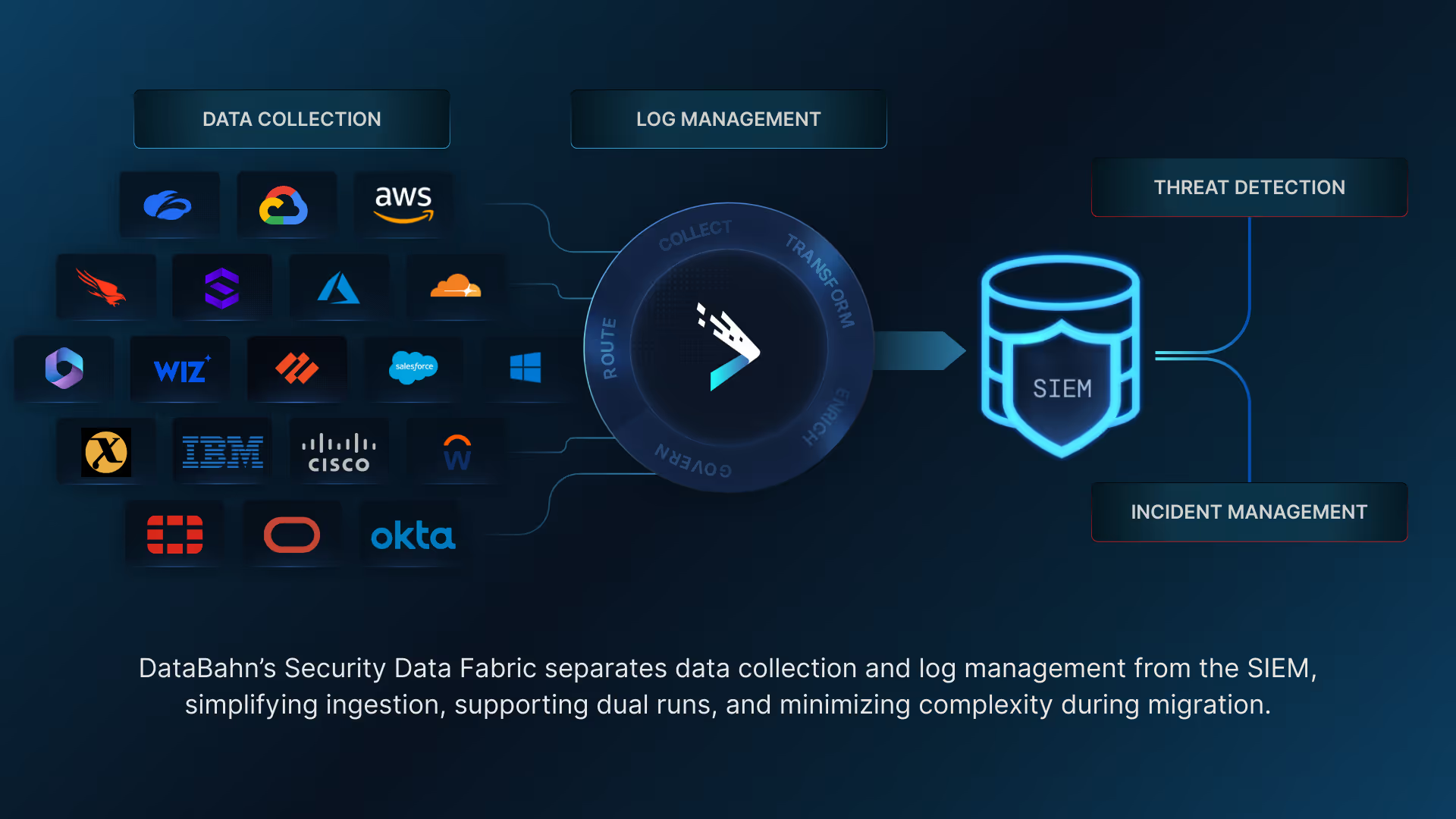
Ingest once, deliver anywhere
Connect your sources to a single, neutral pipeline that streams data simultaneously to both your old and new SIEMs. With our new Smart Agent, you can capture data using the most effective method for each source — deploying a lightweight, programmable agent where endpoint visibility or low latency is critical or a hybrid model where agentless collection suffices. This flexibility lets you onboard sources quickly without rebuilding agents or parsers for each SIEM.
Native format delivery
Route logs in the exact schema each SIEM expects, whether that’s Splunk CIM, Elastic UDM, OCSF, or a proprietary model, without custom scripting. Automated transformation ensures each destination gets the data it can parse and enrich without errors or loss of fidelity.
Dual-run without the overhead
Stream identical data to both environments in real time while continuously monitoring pipeline health. Adjust routing or transformations on the fly so both SIEMs stay in sync through the cutover, without doubling engineering work.
AI-powered data relevance filtering
Automatically identify and forward only security-relevant events to your SIEM, while routing non-critical logs into cold storage for compliance. This reduces ingest costs and alert fatigue while keeping a complete forensic archive available when needed.
Safe, representative evaluation
Send real or synthetic log streams to candidate SIEMs for side-by-side testing without risking sensitive data. This lets you validate performance, rule compatibility, and integration fit before committing to a migration.
Unified Migration Workflow with DataBahn
When you own the data layer, migration becomes a sequence of controlled steps instead of a risky, ad hoc event. DataBahn’s workflow keeps both old and new SIEMs fully operational during the transition, letting you validate detection parity, performance, and cost efficiency before the final switch.
.avif)
With this workflow, migration becomes a controlled, reversible process instead of a risky, one-time event. You keep your SOC fully operational while gaining the freedom to test and adapt at every stage.
For a deeper look at this process, explore our SIEM Migration use case overview — from the problems it solves to how it works, with key capabilities and outcomes.
Key Success Metrics for a SIEM Migration
Successful SIEM migrations aren’t judged only by whether the cutover happens on time. The real measure is whether your SOC emerges more efficient, more accurate in detection, and more resilient to change. Those gains are often lost when migrations are rushed or handled ad hoc, but by putting control of the data pipeline at the center of your migration strategy, they become the natural outcome.
- Lower migration costs by eliminating duplicate ingestion setups, reducing vendor-specific engineering, and avoiding expensive reprocessing when formats don’t align.
- Faster timelines because sources are onboarded once, and transformations are handled automatically in the pipeline, not rebuilt for each SIEM.
- Detection parity from day one in the new SIEM, with side-by-side validation ensuring that existing detections still trigger as expected.
- Regulatory compliance by keeping a complete, audit-ready archive of all security telemetry, even as you change platforms.
- Future flexibility to evaluate, run in parallel, or even switch SIEMs again without having to rebuild your ingestion layer from scratch.
These outcomes are not just migration wins, they set up your SOC for long-term agility in a fast-changing security technology landscape.
Making SIEM Migration Predictable
SIEM migration will always be a high-stakes project for any security team, but it doesn’t have to be disruptive or risky. When you control your data pipeline from end to end, you maintain visibility, detection accuracy, and operational resilience even as you transition systems.
Your migration risk goes up when precursor evaluation relies on small or unrepresentative datasets or when evaluation criteria are unclear. According to industry experts, many organizations launch SIEM pilots without predefined benchmarks or comprehensive testing, leading to gaps in coverage, compatibility, or cost that surface only midway through migration.
To help avoid that level of disruption, we’ll be sharing a SIEM Evaluation Checklist for modern enterprises — a practical guide to running a complete and realistic evaluation before you commit to a migration.
Whether you’re moving to the cloud, consolidating tools, or preparing for your first migration in years, pairing a controlled data pipeline with a disciplined evaluation process positions you to lead the migration smoothly, securely, and confidently.
Download our SIEM Migration one-pager for a concise, shareable summary of the workflow, benefits, and key considerations.



%20(5).avif)


.png)

.png)
.png)





.avif)

.avif)








