Even as CISOs and SOCs are under tremendous pressure to secure their businesses against the rising tide of increasingly sophisticated cyberattacks. Most enterprise Security Operations Centres (SOCs) and Chief InformationSecurity Officers (CISOs) continue to rely on Security Information and EventManagement (SIEM) solutions; however, the dynamic and changing digital environment is making SIEMs, particularly older SIEM systems, increasingly challenging for the teams managing them.
While a vast majority of enterprises (80%+) utilise SIEMs as one of the core foundational tools in their security stack, legacy SIEMs present a significant challenge to SOC efficiency. Legacy SIEMs were designed as monolithic, on-premise aggregators of security logs and can severely impede SOC operations today, which require a more flexible approach. In this piece, we shall take a critical look at the drawbacks of legacy SIEMs and propose a modular approach to future-proof SIEM and SOC operations for enterprises.
Why are legacy SIEMs a problem?
SIEMs were first developed in the early 2000s for enterprises that managed their computing infrastructure and software they owned and operated, typically within their own office space. The term “SIEM” was coined by Gartner in 2005; however, early SIEM products date back to 2000, when ArcSight was released. Legacy SIEMs focus on log collection, rule-based correlation, and manual investigation workflows.
These systems were not designed to manage cloud-based platforms where data volumes have expanded and scaled. Security logs must be collected from digital devices and endpoints that are not limited by geographic boundaries. They are restricted in their scalability, speed, and adaptability to modern cloud-native environments and threats. These limitations arise from the fundamental design of these tools, leading to various challenges. Some of these challenges are:
Cloud and Hybrid Environments
Legacy SIEMs face substantial limitations in integrating with cloud-based environments and emerging technologies, such as containers, microservices, and serverless systems, as well as with new network architectures. Most of these SIEMs lack the necessary solutions and modules, like APIs, connectors, or native support, to ingest data from modern cloud and hybrid platforms seamlessly. SOCs must invest considerable engineering resources and expenses to link legacy SIEMs to an evolving cloud-native environment and maintain those telemetry pipelines.
Connecting and Collecting Security Data and Logs
Legacy SIEMs require point-to-point integration within a vast, complex, and diverse technological ecosystem. Maintaining these integrations over time demands ongoing engineering effort. There are no pre-built integrations for connecting SIEMs to commercial off-the-shelf solutions, and integrating with and managing data ingestion from custom in-house applications and microservices is even more challenging. Additionally, they lack telemetry pipeline health tracking to detect and resolve any disruptions in the pipeline.
Data Ownership and Avoiding Lock-in
Legacy SIEMs were designed to store all your security data and continue to serve as the all-purpose repository for numerous enterprises today. Many enterprises face complex data retention regulatory requirements, which bind them to their SIEM solution until the data retention requirement period has elapsed. Legacy SIEMs lack the flexibility and analytics capabilities in data storage that modern cloud-based data lake solutions offer, creating a significant opportunity cost in utilising SIEMs for storage.
Data Formats and Standardization
Legacy SIEMs were not designed to ingest and parse logs in various formats, then route those data streams in a way and format that downstream platforms can effectively utilise. Parsing, tagging, segmenting, and transforming data into different formats and data models for routing, visibility, and analytics consumes considerable data engineering resources. SOCs inevitably determine which data elements to transform, resulting in blindspots and gaps in visibility and management.
Cost Efficiency
SOCs and CISOs face increasing challenges due to ingestion and computational costs that significantly exceed the basic infrastructure expenses for legacy SIEMs. Moreover, data ingestion licenses and storage costs exert additional pressure as data volumes grow at twice the rate compared to IT budgets year-on-year. Beyond the sticker price for legacy SIEMs, the maintenance and updates of older SIEM products involve patch management, tuning, and configuration optimization.
CISOs and SOCs remain attached to their legacy SIEMs because these systems provide context and have been optimized over time to minimize false positive rates. They are also concerned about the uncertainty, costs, and efforts involved in migrating to a new SIEM setup. However, if CISOs and SOCs want to enjoy the right SIEM for them (whether it’s legacy or next-gen) while ensuring that it can keep up with modern security threats, a modular SIEM architecture may be the solution.
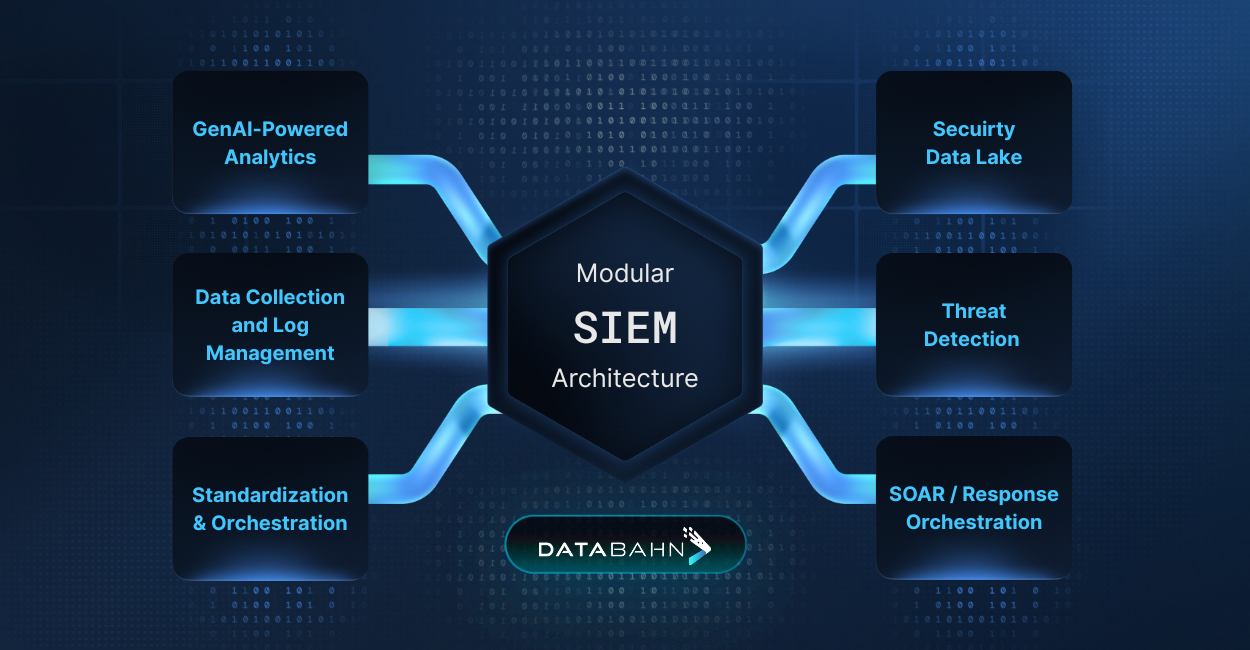
Why should SIEMs be modular?
SIEM platforms serve as comprehensive solutions, incorporating data collection, log management, security data storage, threat detection, and incident response. A modular SIEM architecture divides these functions into separate, independently scalable components, enabling each to develop or be substituted without affecting the overall system. This strategy allows organizations to utilize best-in-class tools for auxiliary functions like log management, storage, and response, while SIEMs focus on their primary strength: advanced threat detection. By separating non-core functions, SIEMs can deliver quicker, more precise threat detection, integrate more seamlessly with other security tools, and scale more effectively to address changing security and compliance demands.
Roadmap for Implementing Modular SIEM Architecture
Phase 1: “Own Your Data – Avoid Vendor Lock-Ins”
Time to deploy – 2 months

This phase separates data ingestion, data storage, and threat detection from the SIEM. This modular approach enables SOCs to select best-of-breed tools while maintaining complete control over their securityinfrastructure. Data ingestion can be managed by a Security Data Fabric orSecurity Data Pipeline Platform, which can handle schema drifts, provide visibility into data flow, connect to various systems and tools, and distributedata to multiple consumers without delays while minimizing ingress and egress costs.
For data storage, decoupling SIEM from storage for non-security-relevant data unlocks significant cost efficiency and analytics capabilities.
1. Event Filtering:
SIEMs only receive pertinent security data to have all the threat models and policies defined.
2. Enterprise Data LakePartitioning
Partition tables within your Enterprise DataLake to host your Security Data Lake, requiring little or no maintenance forthreat hunting capabilities.
3. Pre-processing Data:
Ensure data is parsed before seeding it intothe data lake, making it usable. Dumping raw data into the Security Data Lakeis ineffective; this is a key requirement of the Security Data Fabric /Security Data Pipeline Platform.
4. Cold Storage Utilization:
Push any compliance-related data that is not immediately needed tocold storage, with the ability to replay the data if required.
With only pertinent data going into the SIEM, detection rates shouldimprove while reducing false positives. Threat hunting teams can leverage thecomplete data set in the security data lake needed to perform huntingactivities. A SOAR that integrates with your SDL and SIEM should automatemature processes where required.
Phase 2: Headless SIEMs
Future-proof architecture with lessvendor lock-in
.png)
The Next-Gen adaptive, intelligent HeadlessSIEM architecture focuses on what matters to CISOs — effective threat detection— rather than infrastructure concerns like plumbing and storage. Threatdetection content is leveraged via the power of existing data lake for threatevaluation. A robust, GenAI-enabled SOAR automates responses and streamlinesthreat management.
Phase 3: AI-powered SOC and Data Analytics
Time: POC now with production timeline in 1 year
.png)
Just as CISO organizations seemed to have secured cloud computing and hybrid environments, the emergence of Generative AI is urging security teams to leverage lessons learned from their cloud adoption process to accelerate the protection and integration of this new disruptive technology. Security teams are dedicated to safeguarding generative AI capabilities while seeking methods to harness this technology to enhance their security measures. They aim to avoid limiting their use of Gen AI capabilities to just Co-Pilots.
In today's ever-evolving threat landscape, CISO organizations are tackling various sophisticated threats while managing extensive institutional security data. The combination of this institutional knowledge with AI capabilities transforms enterprise security data into actionable insights. Currently, AI models mainly concentrate on web data, often neglecting the vital insights found within the organization’s security data. The security data fabric, along with the information in the Security data lake, helps bridge this gap by integrating institutional security data with AI, facilitating interaction with insights rather than just presenting irrelevant raw security data. Retrieval-AugmentedGeneration (RAG) enables your security data to be included in the prompts used to query the LLM model, thereby providing valuable detection insights and strengthening your threat-hunting capabilities.
Additionally, integrating Identity, Vulnerability, and GRC data into the security data lake would enhance the efficiency and modularity of the security stack. This approach allows for the use of best-of-breed solutions, facilitating theadoption of new technologies to defend against emerging threats and comply with the fast-changing regulatory landscape. It also ensures full data control while optimizing the security budget.
Value Delivered by Modular SIEM

Future Outlook
The proposed architecture supports an adaptive security posture for the foreseeable future. Security data fabric will become an integral part of the organization, functioning as a centralized data bus. SOAR can truly evolve into a security orchestration and automation platform by not only automating a few incident response playbooks but also streamlining vulnerability ticketing, quarterly access certifications, third-party vendor questionnaires, and GRC metrics reporting, all based on the data orchestrated by the security data fabric.
Conclusion
Today’s consolidated platform approach comes with a significant risk of vendor lock-in at the cost of innovation when the threat landscape is changing at a rapid pace. Leading security market players should embrace standards so that the data is interoperable on any SIEM platform rather than locking their customers with a proprietary data format and making it difficult to switch SIEM providers. The SIEM vendor that builds adapters to seamlessly operate on existing proprietary formatted log data from other impacted SIEM vendors due to consolidation will take the market share faster than consolidated platforms.
The current SIEM market consolidation will force CISO organizations to fast-track adoption of flexible, modular, future proof security architecture. By standardizing log data collection and ingestion, segmenting data storage based on usage leveraging standardized format and adopting innovative best-of-breed threat detection capabilities on top of standardized data, the organizations will be well positioned to take advantage of emerging technologies just as the threat actors are doing. This will help the CISO organizations to stay toe-to-toe with threat actors, if not a step ahead.